Sturdy Security
At Sturdy, the security and integrity of our customer’s information is of the utmost importance.

"If I had been monitoring these Signals a month ago, we would have been able to stop them from becoming escalations."
Sturdy isn’t just another AI wrapper or dashboard. It’s a proven platform delivering measurable results across industries for over four years.
Keeping it secure
Sturdy has developed and maintains a comprehensive Information Security Management program to manage risks to the security, availability, confidentiality, integrity, and privacy of Sturdy systems and products. Our program has been independently audited and certified to meet the requirements of Trust Services Criteria SOC2 Type II.

GDPR Compliant
Sturdy psuedonomizes, anonymizes, and redacts PII to protect your customers’ data. This allows us to train our machine-learning models in a fully anonymized form. It allows our customers the peace of mind that only they have access to their original data.

Infrastructure
Sturdy utilizes Amazon Web Services (AWS) as the Infrastructure-as-a-Service hosting provider. All data stored in AWS data centers located in the United States. Communications into our services are encrypted-in-transit and data is stored encrypted-at-rest using industry standard encryption mechanisms.

Development
Sturdy products are designed with security in mind from the architecture phase. Development teams follow an agile Software Development Life Cycle comprised of source code configuration management, integrated peer review processes, and multi-stage/multi-environment continuous integration, including automated unit, functional, and integration testing and security scanning.

Easy integration with the best apps in just a couple of clicks
FAQs

Feel free to reach out — our team is here and happy to help.
Sturdy ingests communications from multiple systems including Gmail, Outlook, Slack, Zoom, Salesforce, HubSpot, Gainsight, Zendesk, ServiceNow, and Jira, then converts the unstructured text into normalized, deduplicated and linked records [1]. This process eliminates manual ETL requirements and produces a structured “signal stream” from calls, tickets, chats, and emails. Every sentence and word within these interactions is tagged with metadata such as churn risk, sentiment, feature requests, account health, and bug reports [2]. The unified dataset is accessible through both dashboards and a single API that exposes all communication-derived fields [3]. This allows downstream use in BI tools, custom applications, or direct automation within Jira and CRM systems. By converting approximately 80% of formerly unstructured business data into structured analytics-ready material [4], Sturdy creates what it describes as a ready-made “system of intelligence” for enterprises.
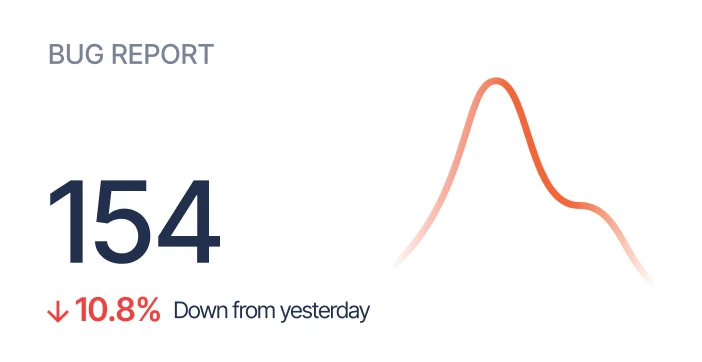
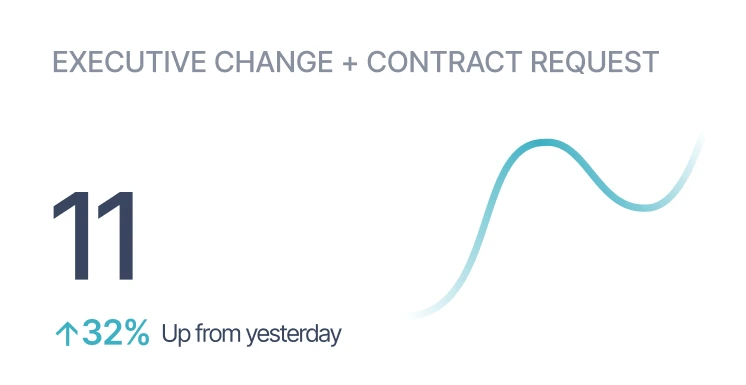
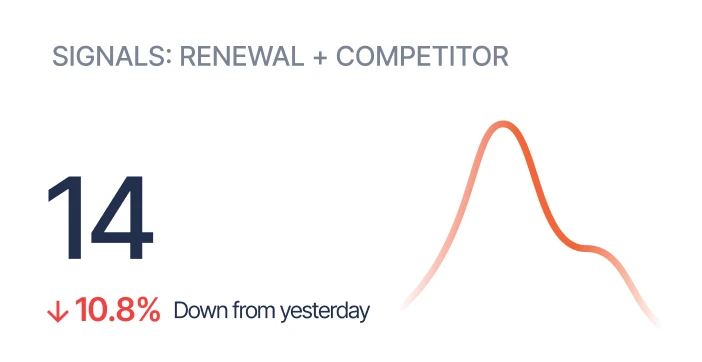
The platform embeds NLP-driven classifiers that continuously read all customer conversations and tag them with over a dozen intelligence categories including bug reports, dissatisfaction, feature requests, and escalation risks [5]. It can automatically flag churn scenarios such as executive turnover, billing disputes, or contract negotiations, while also detecting upsell triggers such as expansion discussions or product demand [6]. Alerts and tickets are sent directly to designated teams, eliminating lag between identification and action. Sturdy integrates tightly with systems like Jira, enabling auto-creation of product bug tasks when repeated error mentions are classified by the models [7]. The framework supports configurable custom AI agents, permitting organizations to define new data triggers through its API and have them monitored without retraining existing models [8]. By capturing every channel under a common analysis engine, Sturdy ensures that signals are unbiased and not constrained to single sources like NPS surveys [9]. This unified approach enables broad pattern detection at enterprise scale.
Sturdy Connect™ enables native integration with tools such as Outlook, Gmail, Slack, Zoom, Salesforce, ServiceNow, Zendesk, HubSpot, and Gainsight in a matter of minutes [10]. These vetted connectors do not require additional licensing and permit immediate ingestion of enterprise workflows into the analytics engine [11]. The resulting cleansed dataset is also available through an API that consolidates all source-native records, linking related conversations and revealing metadata in a normalized schema [12]. This enables IT to embed the signal data directly into Tableau, dashboards, or custom-developed business applications without needing manual exports. Because all interactions are pre-processed for quality and consistency, downstream analytics consume uniform, structured records instead of raw unstructured transcripts. Direct integrations extend to workflow triggers, such as automatically creating Jira issues or sending action assignments to collaboration channels [7]. The platform architecture is designed for rapid deployment, with implementation typically requiring no more than one hour of IT time to launch [13].
The product is operated as a SaaS solution hosted on AWS infrastructure in the United States and is aligned with standard enterprise-grade practices for encrypted data handling [14]. All communications are pseudonymized and anonymized to redact personally identifiable information, an approach that exceeds GDPR requirements and prevents raw data from being disclosed outside an enterprise’s approved use [15]. The vendor maintains a SOC 2 Type II–certified information security program that guides all operational policies [16]. Development processes follow strict SDLC practices, including automated tests, peer code reviews, and continuous vulnerability scanning [17]. Because sensitive inputs are anonymized before analysis, organizations using Sturdy maintain compliance with strict data privacy regulations. This architectural approach creates a controlled environment where encrypted data is only accessible by customer-approved entities. Auditability is embedded within the procedures, giving enterprises confidence in managing compliance posture for both regulatory and corporate security standards.
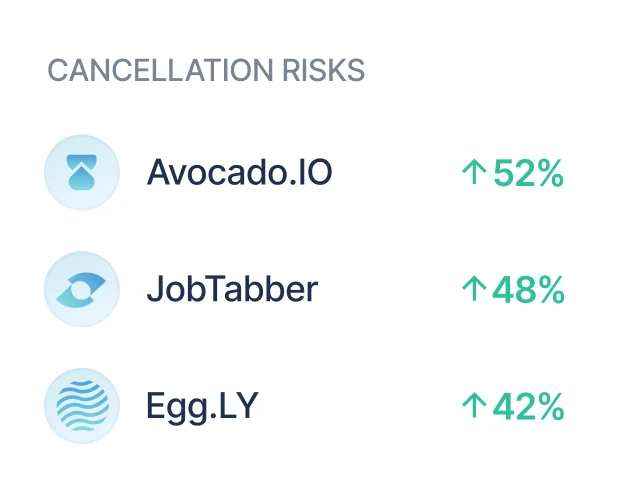
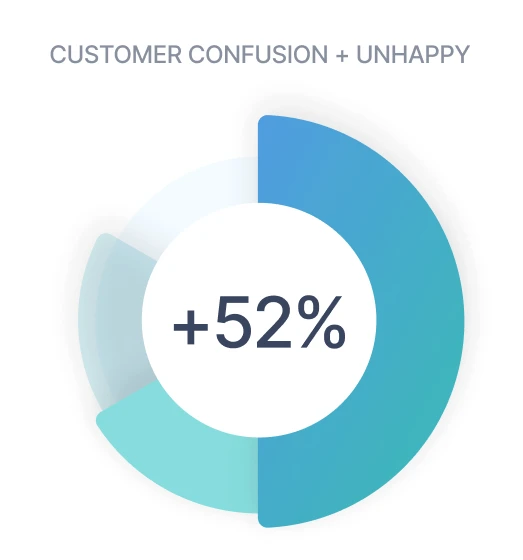
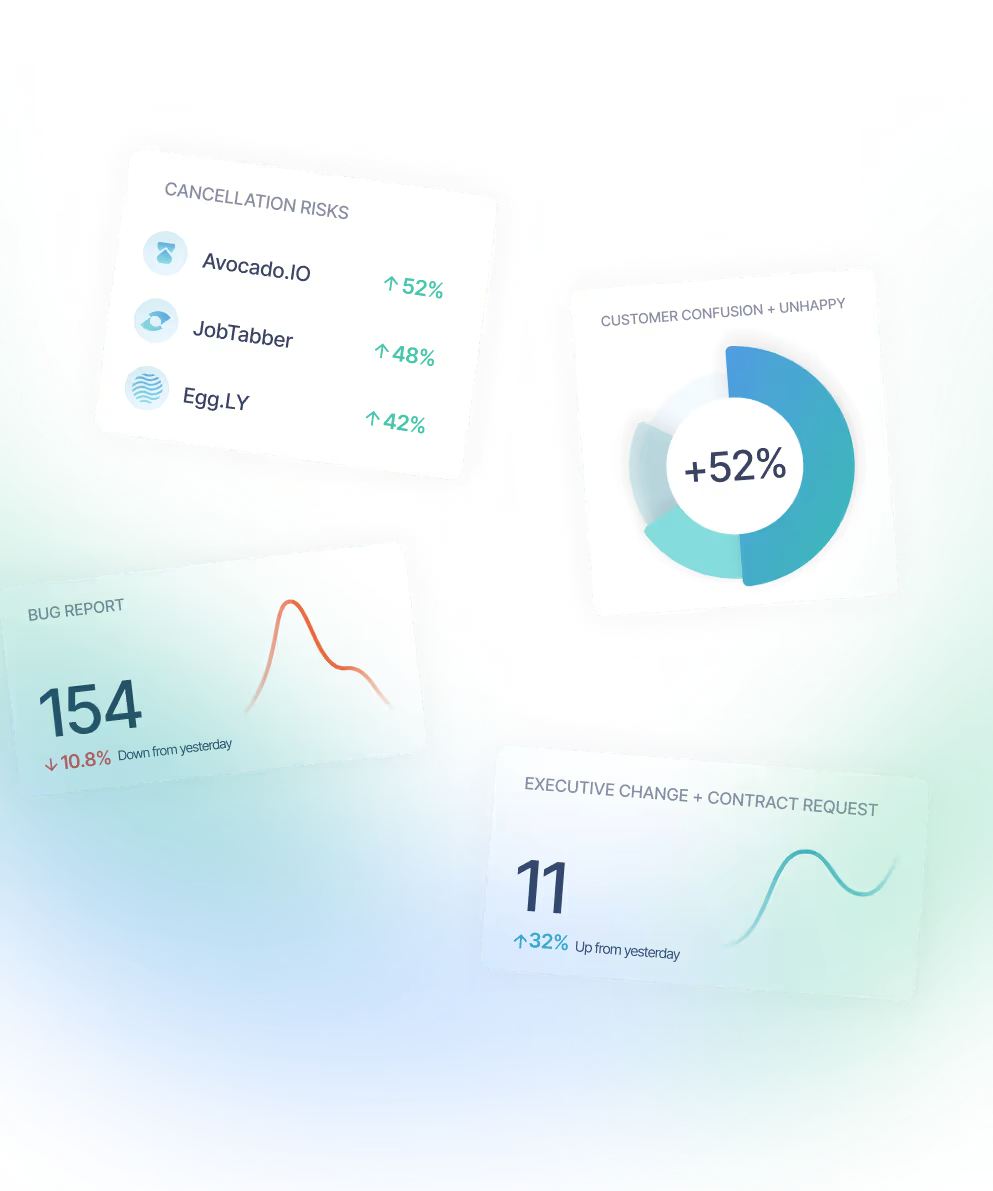
Deployments of Sturdy have reported substantial improvements in account stability and retention metrics. One organization documented 100 percent retention across a portfolio exceeding 100 customer accounts after leveraging the continuous signal monitoring provided by the platform [18]. Another reported a 30 percent month-over-month increase in retention within six weeks of implementation, attributing the improvement to timely action on churn indicators [19]). Case studies illustrate precise examples such as identifying that a single product line accounted for 84 percent of customer confusion and dissatisfaction, allowing proactive remediation [20]. By surfacing issues like feature confusion or unacknowledged bug reports directly to responsible teams, Sturdy mitigates account risk and improves customer experience. Its predictive churn models also enhance renewal pipeline accuracy by quantifying account health through rich signal capture rather than relying only on surveys [21]. The economic impact extends beyond retention, as even a one percent reduction in churn tied to Sturdy's insights can meaningfully elevate customer lifetime value across multimillion-dollar portfolios [22]. Evidence from customer testimonials indicates that teams can act on signals in real time to prevent cancellations that otherwise would not have been caught [23]. This demonstrates a direct correlation between Sturdy’s analytics capability and measurable business outcomes.